
The
'Elizabeth Swann' cruising up the
Amazon,
seen here in normal low-drag hull mode, with solar wings
tilted down on both sides, about 20-30 degrees from
horizontal, but not in full stealth mode. The hulls are not
flooded.
The
Elizabeth
Swann is a virtual 'stealth' ship due to the ability of
the large solar
wings surfaces, to change the angle they presents to the
sun - independently of one another. Coupled with the ability of the vessel to
lower itself into the water
to reduce shipboard surface area presented to the wind, by
flooding her hull tanks (compartments
in the trimaran sponsons) actually for use as a
sea-anchor in storm
conditions. In addition, the electric
waterjet drives reduce the sonar signature, making the sound
waves linearly directional, as opposed to an unguarded general
sound broadcast, as in a traditional ship, open revolving propeller
design.
These
features, when combined, can make the ship virtually undetectable to
radar and sonar as per the diagrams below.
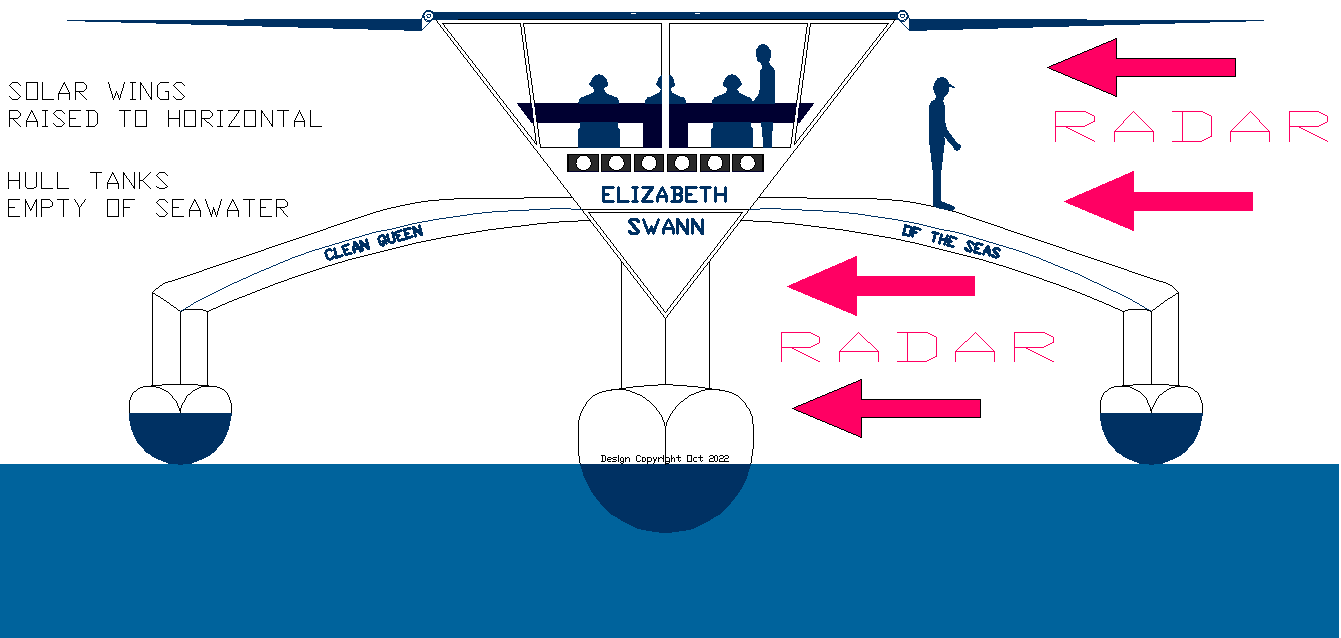
The
'Elizabeth Swann' is seen here with her solar wings
horizontal, and her hulls empty of seawater for normal (low
drag) running in displacement mode. The ship is much more
visible to radar sets on other ships and land based tracking
stations.
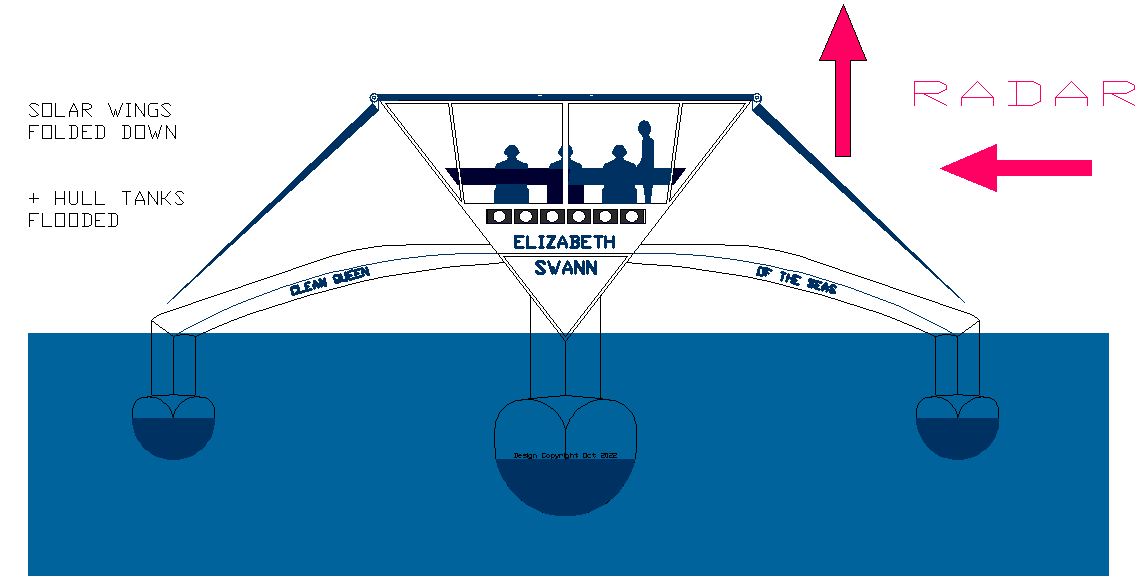
The
'Elizabeth Swann' is seen here with her solar wings folded
down low, with her hull tanks filled with seawater, so that
she sinks down into the sea, and presents a smaller
freeboard. The angle of the solar wings deflects radar
(radio waves) making the ship invisible to other ships and
land bases.
This
is more of an advantage to other (for example) military ships that cannot alter
their form, by virtue of fixed hull and superstructure panels, and
fixed displacement. For example, the Elizabeth
Swann can change the angle of large wing-panels at will,
to be visible to radar at one moment, then invisible a few
minutes later. That is much more confusing to an enemy, than
a ship that has reduced visibility all of the time. Because,
if a ship is visible to radar, the enemy will think they can
track it and feel safe that they know where it is. Then if
it suddenly disappears, confusion sets in. Because the ship
could have sunk or changed course, when in reality its radar
footprint has changed - seemingly impossible in conventional
thinking. The Elizabeth
Swann is the first (and we think only) ship in the world
to have these features. She has what the designer calls an
"active" hull.
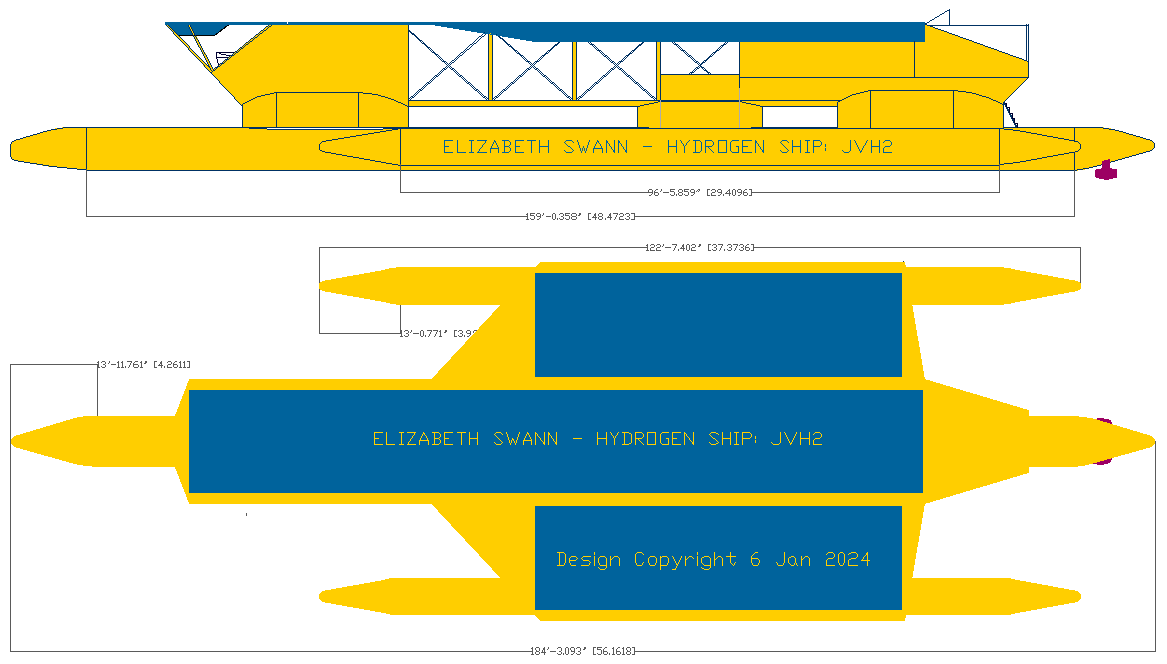
UNIQUE
The Elizabeth Swann solar and hydrogen powered ship is described as unique because it incorporates what is termed "variable stealth technology" using an innovative "active hull" design. This system allows the vessel to reduce its radar footprint through dynamic, real-time modifications to its structure—a feature that sets it apart from conventional designs. In particular, the stealth mode is said to operate in two primary ways:
1. Deflection via Solar Wing Adjustment: The ship is equipped with
solar wings whose angles can be altered. By changing these angles, the vessel is able to deflect incoming radar waves, thereby reducing the strength of the radar signal that is reflected back to the source. This clever use of solar panel orientation serves a dual purpose: it not only harvests energy for propulsion but also acts as a stealth mechanism by scattering radar signals in undesirable directions.
2. Active Hull Reconfiguration: The concept of an "active hull" implies that the ship can make further adjustments to its hull shape or use specialized materials to absorb or redirect radar waves. The reconfigurable hull likely employs advanced engineering techniques—possibly including dynamic surface patterns or variable geometries—to further minimize its radar cross-section.
3. Submerged Hull Concept: Another fascinating aspect of the design involves a central hull that is intentionally flooded, or designed as a
SWATH (Small Waterplane Area Triple Hull)
configuration SWATH normally meaning: Small Waterplane Area
Twin Hull. This approach allows the vessel to sink lower into the
water compared to conventional stealth hulls. No other ship is known to have such features, except of course submarines, that can submerge below the waves completely.
This innovative approach represents an intriguing fusion of renewable energy technology with stealth design principles. The integration of solar power and variable stealth capabilities is particularly compelling in an era where sustainable yet high-performance vessels are
increasingly in demand. While technical specifications and full operational details may still be under development or in conceptual stages, these features hint at a future where adaptive design can offer both environmental benefits and strategic advantages.
Useful in the Treasure Island adventure, when dodging the British
Royal Navy and Spanish
Armada blockades. In actuality, saving these navies from
themselves, being hopelessly outclassed by the Elizabeth
Swann's Excalibur
weapon during a nighttime encounter.
One
might imagine how useful this ability may be in a World
War Three situation, or how vulnerable an ordinary Russian
surface warship might be to Ukrainian
drones in the present conflict, that has NATO
worried as to nuclear
escalation, as, if and when Vladimir
Putin runs out of soldiers or conventional weapons that
are not making the grade. Where Volodymyr Zelenskyy
is proving to be more quickly adaptable, in taking on unadventurous
vessel designs and tanks that have not evolved much since
the Second
World War.

1985
- Not exactly the prettiest of ships, the US Navy's
experimental 'Sea Shadow' was one of the first truly
radar invisible vessels. But where are the weapons?
STEALTH SHIPS
A stealth ship is a ship which employs stealth technology construction techniques in an effort to ensure that it is harder to detect by one or more of radar, visual, sonar, and infrared methods.
These techniques borrow from stealth aircraft technology, although some aspects such as wake and acoustic signature reduction (acoustic quieting) are unique to stealth ships' design. Though radar cross-section (RCS) reduction is a fairly new concept many other forms of masking a ship have existed for centuries or even millennia.

SHAPE OF STEALTH SHIPS
n designing a ship with reduced radar signature, the main concerns are radar beams originating near or slightly above the horizon (as seen from the ship) coming from distant patrol aircraft, other ships or sea-skimming anti-ship missiles with active radar seekers. Therefore, the shape of the ship avoids vertical surfaces, which would perfectly reflect any such beams directly back to the emitter. Retro-reflective right angles are eliminated to avoid causing the cat's eye effect. A stealthy ship shape can be achieved by constructing the hull and superstructure with a series of slightly protruding and retruding
surfaces. Furthermore, round shapes on the ship are eliminated or covered up, examples include smokestacks and gun turrets. Also, cavities that present a horizontal face are to be eliminated since they act like a trap and are very visible to radar. To get around these limitations many ships use features such as panels that cover reflective surfaces or use alternate designs of hardware. Also, every effort must be made to have the smallest gaps on the ship as possible. Hull shapes include tumblehome hull designs which slope inward from the waterline, and
small-waterplane-area twin hulls (SWATH) which allow for better stability when using a tumblehome hull. These RCS design principles were developed by several navies independently in the 1980s using work done on aircraft RCS reduction as the starting point.
The currently developed U.S. Zumwalt-class destroyer — or DD(X) — is the US version of a stealth ship. Despite being 40% larger than an Arleigh Burke-class destroyer the radar signature is more akin to a
fishing boat, according to a spokesman for Naval Sea Systems Command; sound levels are compared to the
Los Angeles-class
submarines. The tumblehome hull reduces radar return and the composite material deckhouse also has a low radar return. Water sleeting along the sides, along with passive cool air induction in the
back reduces infrared signature. Overall, the destroyer's angular build makes it "50 times harder to spot on radar than an ordinary destroyer.
The Swedish Navy's Visby class corvette is designed to elude visual detection, radar detection, acoustic detection, and infrared detection. The hull material is a sandwich construction comprising a PVC core with a carbon fibre and vinyl laminate. Avoidance of right angles in the design results in a smaller radar signature, reducing the ship's detection range.
Britain's Type 45 anti-air warfare destroyer has similarities to the Visby class, but is much more conventional, employing traditional steel instead of carbon fiber. Like Visby, its design reduces the use of right angles.
Taiwan's' Tuo Chiang-class stealth corvette are a class of fast stealth multi-mission corvettes currently in service with the Republic of China (Taiwan) Navy. The ships are designed to have a low radar cross-section and evade radar detection making it difficult to detect the ship when operating closer to the coastline.
Sea Shadow, which utilizes both tumblehome and SWATH features, was an early U.S. exploration of stealth ship technology.

SIGNATURE REDUCTION
Stealth technology represents more than just a low RCS; noise reduction plays a huge role in naval stealth because sound travels much better in water than air. Some of the techniques used include muffled exhaust systems, modified propeller shapes, and pump-jets. The shape of the hull can also have a great effect on the reduction of the noise from a ship. Another major element is signal emission control. Modern warships emit much electromagnetic radiation in the form of radar, radio, and even bleed-off from the ship's electrical systems. All of this can be used to track a ship and thus modern stealth ships often have a mode that switches off many of the electronic emissions, the downside of course is that the ship then has to rely on passive sensors and can't easily send messages further than line of sight.
Also of great importance are thermal emissions. A heat signature can make a ship stand out like a candle in a dark ocean making it easier to spot and because it is possible to see infrared emissions through features that would normally hide a ship such as fog, or a smoke screen, many detection platforms like patrol aircraft, UAV's, and satellites often have the ability to see multiple bands in the infrared spectrum including heat. This necessitates the control of these emissions. The most common way is to mix any hot gasses emitted by the main source of heat which is the engines exhaust with cold air to dilute the signature and make it harder to pick out the ship from the background warmth. Another method vents the exhaust into the water though this increases the ship's acoustic signature. For the hull water can be actively distributed across the hull of the ship cooling the ship. Another less crucial but still relevant part of a stealth ship is visual camouflage. This area is probably the oldest form of stealth, with records going back almost as far as the writing of ancient mariners using visual tricks to make their ships harder to spot. Though still relevant this area has taken on lesser importance with the advent of long-range radar.
EXAMPLES OF FULL STEALTH SHIPS
Sea Shadow (IX-529) – American experimental stealth ship (1985, experimental platform)
La Fayette-class frigate – French general purpose stealth frigates (1996)
Hamina-class missile boat – Fast attack craft class of the Finninh Navy (1998)
Skjold-class corvette – Light, fast, stealth missile corvettes of the Royal Norwegian Navy (1999)
Type 22 missile boat – Ship class in the Chinese People's Liberation Army Navy (2004)
Formidable-class frigate – Frigate class of the Republic of Singapore Navy (2007)
Visby-class corvette – Swedish stealth missile corvettes (2009)
Klewang-class – Stealth trimaran fast attack craft of Indonesian Navy fast attack craft (2010)
Independence-class littoral combat ship – US Navy small coastal combat ships (2010)
Ada-class corvette – Turkish anti-submarine ships (2011)
Tuo Chiang-class Stealth Corvette – Taiwanese class of war vessel (2014)
Zumwalt-class destroyer – Stealth missile destroyer class of the US Navy (2016)
Gowind-class design – French multi-role ship design (2017)
Type 055 destroyer – Class of guided missile stealth cruisers/destroyers of the Chinese People's Liberation Army Navy (2020)

STEALTH
AIRCRAFT - CANNOT CHANGE OR VARY THEIR RADAR SIGNATURE
Since radar-directed defenses began taking a toll of bomber formations in
World War
II, aircraft designers and military aviators have sought ways to avoid radar detection. Many materials of the early jet age were known to absorb radar energy rather than reflect it, but they were heavy and not strong enough for structural
applications. It was not until after the 1960s and ’70s, with the development of such materials as
carbon-fibre composites and high-strength plastics (which possessed structural strength as well as being transparent or translucent to radar), that radar signature reduction for piloted combat aircraft became possible.
While no aircraft is totally invisible to radar, stealth aircraft make it more difficult for conventional radar to detect or track the aircraft effectively, increasing the odds of an aircraft successfully avoiding detection by enemy radar and/or avoiding being successfully targeted by radar guided weapons. Stealth is the combination of passive low observable (LO) features and active emitters such as low-probability-of-intercept radars, radios and laser designators. These are usually combined with active measures such as carefully planning all mission maneuvers in order to minimize the aircraft's radar cross-section, since common actions such as hard turns or opening bomb bay doors can more than double an otherwise stealthy aircraft's radar return.
The existence of a Stealth program, designed to produce aircraft that were effectively immune to radar detection at normal combat ranges, was announced by the U.S. government in 1980. The first aircraft employing this technology, the single-seat Lockheed F-117A Nighthawk ground-attack fighter, became operational in 1983. The second was the Northrop B-2 Spirit strategic bomber, which first flew in 1989. Both aircraft had unconventional shapes that were designed primarily to reduce radar reflection. The B-2 was of a flying-wing design that made it only slightly longer than a fighter yet gave it a wingspan approaching that of the B-52, while the F-117A had a short pyramid-shaped fuselage and sharply swept wings.
Stealth aircraft are typically more expensive to develop and manufacture. An example is the B-2 Spirit that is many times more expensive to manufacture and support than conventional bomber aircraft. The B-2 program cost the U.S. Air Force almost $45 billion.
Reducing radar signature also required controlling shape, particularly by avoiding right angles, sharp curves, and large surfaces. In order to direct radar energy in the least-revealing directions, the external shape of a stealth aircraft was either a series of complex large-radius, curved surfaces (as on the B-2) or a large number of small, flat, carefully oriented planes (as on the F-117A). Fuel and ordnance were carried internally, and engine intakes and exhausts were set flush or low to the surface. To avoid interception of radar emissions, stealth aircraft had to rely on inertial guidance or other
non-emitting navigational systems.

OPERATIONAL STEALTH AIRCRAFT
The U.S. and Israel are the only countries to have used stealth aircraft in combat. These deployments include the United States invasion of Panama, the first Gulf War, the Kosovo Conflict, the War in Afghanistan, the War in Iraq and the 2011 military intervention in Libya. The first use of stealth aircraft was in the U.S. invasion of Panama, where F-117 Nighthawk stealth attack aircraft were used to drop bombs on enemy airfields and positions while evading enemy radar.
In 1990 the F-117 Nighthawk was used in the First Gulf War, where F-117s flew 1,300 sorties and scored direct hits on 1,600 high-value targets in
Iraq while accumulating 6,905 flight hours. Only 2.5% of the American aircraft in Iraq were F-117s, yet they struck 40% of the strategic targets, dropping 2,000 tons of precision-guided munitions and striking their targets with an 80% success rate.
In the 1999 NATO bombing of Yugoslavia two stealth aircraft were used by the United States: the veteran F-117 Nighthawk, and the newly introduced B-2 Spirit strategic stealth bomber. The F-117 performed its usual role of striking precision high-value targets and performed well, although one F-117 was shot down by a Serbian Isayev S-125 'Neva-M' missile commanded by Colonel Zoltán Dani. The then-new B-2 Spirit was highly successful, destroying 33% of selected Serbian bombing targets in the first eight weeks of U.S. involvement in the War. During this war, B-2s flew non-stop to Kosovo from their home base in Missouri and back.
In the 2003 invasion of Iraq, F-117 Nighthawks and B-2 Spirits were used, and this was the last time the F-117 would see combat. F-117s dropped satellite-guided strike munitions on selected targets, with high success. B-2 Spirits conducted 49 sorties in the invasion, releasing 1.5 million pounds of munitions.
During the May 2011 operation to kill Osama bin Laden, one of the helicopters used to clandestinely insert U.S. troops into Pakistan crashed in the bin Laden compound. From the wreckage it was revealed this helicopter had stealth characteristics, making this the first publicly known operational use of a stealth helicopter.
Stealth aircraft were used in the 2011 military intervention in Libya, where B-2 Spirits dropped 40 bombs on a Libyan airfield with concentrated air defenses in support of the UN no-fly zone.
Stealth aircraft will continue to play a valuable role in air combat with the United States using the F-22 Raptor, B-2 Spirit, and the F-35 Lightning II to perform a variety of operations. The F-22 made its combat debut over Syria in September 2014 as part of the US-led coalition to defeat ISIS.
From February 2018, Su-57s performed the first international flight as they were spotted landing at the Russian Khmeimim air base in Syria. These Su-57s were deployed along with four Sukhoi Su-35 fighters, four Sukhoi Su-25s, and one Beriev A-50 AEW&C aircraft. It is believed that at least 4 Su-57 are deployed in Syria. and that they have likely been armed with cruise missiles in combat.
In 2018, a report surfaced noting that Israeli F-35I stealth fighters conducted a number of missions in Syria and even infiltrated Iranian airspace without detection. In May 2018, Major General Amikam Norkin of IAF reported that Israeli Air Force F-35I stealth fighters carried out the first-ever F-35 strike in combat over Syria.
The People's Republic of China started flight testing its Chengdu J-20 stealth multirole fighter around in 2011 and made its first public appearance at Airshow China 2016. The aircraft entered service with the People's Liberation Army Air Force (PLAAF) in March 2017. Another fifth-generation stealth multirole fighter from China, the Shenyang FC-31 has undergone flight testing.

LIST OF STEALTH AIRCRAFT
Dedicated reduced cross section designs in service
B-2 Spirit - (United States)
F-22 Raptor - (United States)
F-35 Lightning II - (United States)
Chengdu J-20 – (China)
Sukhoi Su-57 – (Russia)
HUMAN
SPIES & SPYING
There are several types of soldier who do not qualify as privileged combatants:
- Combatants who would otherwise be privileged but have breached the laws and customs of war (e.g., feigning surrender or injury or killing enemy combatants who have surrendered). The loss of privileges in that case only occurs upon conviction, i.e. after a competent court has determined the unlawfulness of the conduct in a fair trial.
- Combatants who are captured without the minimum requirements for distinguishing themselves from the civilian population, i.e. carrying arms openly during military engagements and the deployment immediately preceding it, lose their right to prisoner of war status without trial under Article 44 (3) of Additional Protocol I.
- Spies, i.e. persons who collect information clandestinely in the territory of the opposing belligerent. Members of the armed forces conducting reconnaissance or special operations behind enemy lines are not considered spies as long as they wear their uniform.
Espionage against a nation is a crime under the legal code of many nations. In the United States, it is covered by the Espionage Act of 1917. The risks of espionage vary. A spy violating the host country's laws may be deported, imprisoned, or even executed. A spy violating its own country's laws can be imprisoned for espionage or/and treason (which in the United States and some other jurisdictions can only occur if they take up arms or aids the enemy against their own country during wartime), or even executed, as
Julius and Ethel Rosenberg were.
CAMOUFLAGE
IN THE
NATURAL WORLD
Many
insects have evolved to use body parts as camouflage. Their exoskeleton
design is almost perfectly suited to such purposes. Where
the body is hard keratin on the outside, as opposed to a
soft skin on the outside and a hard bone skeleton on the
inside. Keratin can be formed into horns or wing cases (in
beetles) or make an insect look like a leaf (praying mantis)
or stick.
Plumage,
fur and feathers give mammals and birds the ability to
disguise themselves, to blend into their surroundings.
Peacock tail feathers give us an example of a massive colour
display used to frighten enemies and as a courtship display.
Zebra have white and black lines in their body hair, as
camouflage to fool big cat predators during a chase. Humpback
whales have large white and grey patterns on their
enormous fins to trick sharks
and killer whales trying to bite them, as to what to aim at.
While from above, they present as dark-grey or blue-black,
to blend into the seascape. In WWII,
aircraft adopted such a two-tone scheme, painted light blue
underneath and field green on top of their wings and
fuselage.
All
of this is survival strategy. Whereas, Leopards and Cheetahs
have spots to disguise them when resting in trees and
stalking prey. Tigers have stripes for hunting in the
jungle, while Lions are plain sandy-brown, to blend into the
African savannah. Yet these large predators from different
continents are so biologically similar, that they can
reproduce, to give Tions or Ligers.
Humans
can alter their appearance in seconds, just by changing
clothes. Humans can also dye the colour of their hair and
wear hats. By changing from jeans and a 'T' shirt, into a
suit, a student can blend in at high level social functions
and fool their peers. An operative who would normally wear a
shirt and tie to work, can put on an overall to mix with
workers.
The
ultimate camouflage for a human is a combat uniform. These
come in many printed colours and designs, depending on the
geographical location of operations. Some are black (night
operations), some white (snow), and some sandy colored with
green leaves. In the field of human conflict, if a spy is
caught wearing the uniform of their enemy, they can
sometimes be shot (despite the Geneva Convention), after a
lawful trial and conviction.
REFERENCES
https://









